![]() Cybersecurity Alerts
Cybersecurity Alerts
Financial Support Phish
October 2, 2024
Clemson users should be aware of another targeted phishing campaign. This one claims to be a University Supported Program and offers to help staff and students with financial support.
Below is an example of one of these types of emails.

 Users are prompted to follow a link within the email, which takes them to a login page that asks them to enter their email address, username and password. They are hoping that you will enter your Clemson account information.
Users are prompted to follow a link within the email, which takes them to a login page that asks them to enter their email address, username and password. They are hoping that you will enter your Clemson account information.
But this is actually a scam designed to steal users’ credentials. If you receive an email similar to this, you should report it using the Report Phishing button in Outlook or by forwarding it to phishing@clemson.edu.
Package Delivery Scam
September 9, 2024
 Since ordering and receiving packages has become commonplace for most people, cybercriminals are trying to take advantage of this practice. One of the ways they do this is by sending you a package with an item from a common online retailer, like Amazon, that you never ordered.
Since ordering and receiving packages has become commonplace for most people, cybercriminals are trying to take advantage of this practice. One of the ways they do this is by sending you a package with an item from a common online retailer, like Amazon, that you never ordered.
This is also known as a Brushing Scam. But the new twist on this scam is that inside your package you will find a QR Code with instructions on how to return the item or to find out more details about the order. Because this item was something that you didn’t actually order, they are hoping that you will scan the QR code that is included in the package.
These QR codes typically take you to a phony website that may load malware on your phone, which could compromise your device, or even steal your information.
For any package return or to get more information about an order, a safer solution would be to go to the vendor’s website yourself by typing in the actual address, rather than trusting a QR coded link. Once you are on the actual vendor’s website, you can check for details on the order or how to legitimately return an item if needed.
But if this was not an item you ordered yourself, then you are not obligated to return it. And you can simply keep it or throw it away.
Here are some tips to help avoid falling for this scam:
- Preview the URL for any QR Code before doing anything
When you scan a QR code with your phone’s camera, it will display the website URL from the QR code. You should look carefully at the URL to see if it matches the official website. And beware of any tricky or misleading letter substitutions in the URL, which may make it similar to the real website address.
- Never download a QR Code Scanning App
You should only use your phone’s camera to scan a QR code. If you are prompted to download any other tool to view the QR Code, this could be another way that scammers can infect your phone with malware.
- If you follow the URL from the QR Code, look for any suspicious signs on the website
Verify that the URL is an HTTPS address and not just an HTTP address. Look for things like low-resolution graphics, misspellings, grammar errors, or anything that looks out of place. Also, be extra cautious if the website asks for any personal information, account login and password data, or credit card information.
Fake Browser Update
August 30, 2024
Users should beware of a current “Update your Browser” type scam. In this scam, cybercriminals will display a full-screen web page or pop-up window with a fake notification saying that your browser is out of date and needs to be updated. The phony page will also include a button to download the supposedly needed update.
If a user clicks on that link, they will actually install malware on their device that the cybercriminals can use to steal data or take control of that device.
 When a legitimate web browser update is needed, this is typically done automatically when the browser is started. It is also important to remember to completely close and shut down your browser after each session, as well as reboot your computer on a regular basis. You can also verify if any browser updates are needed by checking the settings section in your browser.
When a legitimate web browser update is needed, this is typically done automatically when the browser is started. It is also important to remember to completely close and shut down your browser after each session, as well as reboot your computer on a regular basis. You can also verify if any browser updates are needed by checking the settings section in your browser.
Clemson users can contact the CCIT Support Center for additional help.
OneDrive Users Targeted
July 31, 2024
The Trellix Advanced Research Center has discovered a sophisticated phishing campaign that specifically targets OneDrive users.
In this campaign, users receive an email that contains a .html (web page type) file. When that file is opened, the user will see something like the image below, which simulates a Microsoft OneDrive page with an error message.
 (image via Trellix.com)
(image via Trellix.com)
The blue fake error message pop-up will say that there is a DNS issue with the user’s OneDrive. And the error display has two buttons. The “Details” button will actually take users to the real Microsoft web page for troubleshooting a DNS issue. But if a user clicks on the “How To Fix” button, it will launch a JavaScript program embedded within the HTML file. That JavaScript will display additional misleading instructions for the user. If followed, the result will be unknowingly downloading malware onto the user’s computer.
This particular attack uses misleading visual elements and a sense of urgency as its attack vector. For additional information, please see the full article at: https://www.trellix.com/blogs/research/onedrive-pastejacking/
Student Loan Phishing Email
July 18, 2024
Clemson students are being targeted with a new phishing email that references paying off Student Loans. One unique element of these emails is that they contain the student’s name and their home mailing address. These phishing emails were sent to students via their g.clemson or clemson.edu accounts.
Students are prompted to call a phone number that would most likely result in being asked to verify some more personal information which the cybercriminals could also use as part of their scheme. Typically, their goal is to steal money.
There were several indicators that this was not a legitimate email:
- The sender’s address is a generic Hotmail account.
- It has a “too good to be true” theme.
- There is also a sense of urgency prompting users to respond quickly, which is a common tactic because they are hoping that you won’t be thinking clearly if you are in a hurry.
If students receive an email like the one below, they should report it by clicking on the “Report Phishing” button in Outlook or forwarding it to phishing@clemson.edu.

Social Engineering Calls
June 21, 2024
 Clemson University is seeing an increase in voice phishing, also known as vishing. Vishing is a social engineering tactic done through phone calls where the caller uses deception and manipulation.
Clemson University is seeing an increase in voice phishing, also known as vishing. Vishing is a social engineering tactic done through phone calls where the caller uses deception and manipulation.
The goal of the vishing phone call is to pose as someone they are not and then to gain access to someone’s account or service. Once the cybercriminals have access to your account, they can change passwords to lock you out of your own account as well as transfer data or even funds from your financial institution.
For example, you may get a call from someone saying they are from your bank, and that they are seeing some potentially fraudulent charges on your credit card. Then, they may ask you to verify some of your information, such as your mailing address, birth date, or account number. Once they have some of that key information, they could then call your actual bank and claim to be you. When your real bank asks for some of your personal information to verify that it is really you calling, the cybercriminals can provide that information because you just gave it to them.
Another example would be someone calling a Support Desk asking for help in resetting their password. When the support person asks them to confirm their identity by sending something to the user’s phone, the fake caller could make up some excuse about how they lost their phone, which is why they are calling to reset their password. The Support Desk employee who is trying to be helpful may then let them skip that step. The cybercriminals sometimes will even research personal details on their victims from social media to help them answer other key information if asked.
To help reduce the risk of becoming a victim of vishing, it is recommended that you don’t answer calls from unknown numbers on your personal phone. If you do get a message or call claiming that there is an urgent issue, like an alert from your financial institution, a billing issue from a service that you use, a family medical emergency, or even someone asking you to do something for them, don’t necessarily trust the validity of that call.
It is always better to verify the information yourself. Hang up from that call and then call the institution, service, or person who supposedly just called you to verify whether the issue is legitimate. Don’t trust that the caller is who they say they are. And verify first, before giving any information or taking any action.
Apple Reset Attacks
March 27, 2024
Recently, some Apple users have fallen under a cyber-attack called “Push Bombing” or “MFA (multi-factor authentication) Fatigue”.
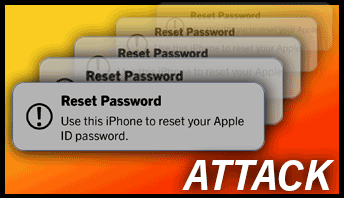 In these attacks, Apple users are repeatedly sent a push notice to Allow or Deny a password reset on their Apple account. Sometimes, a user may receive 100 or more of these notifications, and those notifications can show up on all your Apple devices. If a user allows one of these password resets, then the scammers can change your password and lock you out of your account.
In these attacks, Apple users are repeatedly sent a push notice to Allow or Deny a password reset on their Apple account. Sometimes, a user may receive 100 or more of these notifications, and those notifications can show up on all your Apple devices. If a user allows one of these password resets, then the scammers can change your password and lock you out of your account.
Even if a user denies all of the prompts, they may still get a phone call from scammers claiming to be from Apple Support, because the scammers know the phone number associated with the user’s Apple account.
The purpose of the scammer’s call is to try to get the user to initiate a request for an Apple ID reset code which is sent to the user’s device as a text message that includes a one-time password. If the user supplies that one-time code to the fake Apple Support caller, the attackers will use that information to reset the password on the user’s account and lock the real user out of their own account. Once the scammer has control of your account, they can also remotely wipe all of your Apple devices.
If you did not initiate a password reset yourself on your Apple device, you should always deny those prompts. And if you get a call from someone claiming to be an Apple Support person, be aware that Apple never initiates outbound calls to customers, unless the customer has first requested to be contacted. So, in those situations, hang up on the person who called you, and then contact the official Apple Support Center yourself to see if there really is an issue. You can’t trust that a caller really is who they say they are.
For more information, please see the article at:
https://krebsonsecurity.com/2024/03/recent-mfa-bombing-attacks-targeting-apple-users/
Fake Student Job Email
February 12, 2024
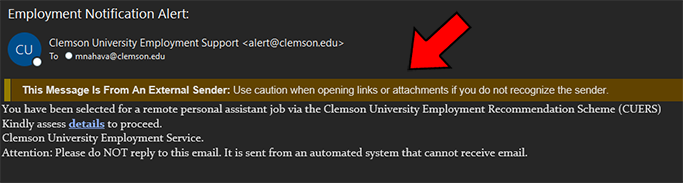
Clemson students are again being targeted with a new phishing email campaign about a fake job offer. In these emails, the cybercriminals are spoofing various Clemson email sender addresses, such as “alert@clemson.edu” or “employment_services@my.clemson.edu” making it appear that it is coming from a real Clemson.edu account.
One of the clues that these are not legitimate Clemson emails is that Outlook users will see that these emails have been flagged with the External Sender banner at the top of the email, which indicates that this email did not actually come from an internal Clemson email account.
Also, be aware that Clemson does not typically reach out to students with job offers in this manner.
These phishing emails include a link where users are asked to enter their Clemson login and password information which will then be stolen by the cybercriminals and used in their attack.
If you entered your Clemson credentials into their fake web page, it is recommended that you immediately reset your password and notify the CCIT Support Center at (864) 656-3494 or ITHelp@clemson.edu.
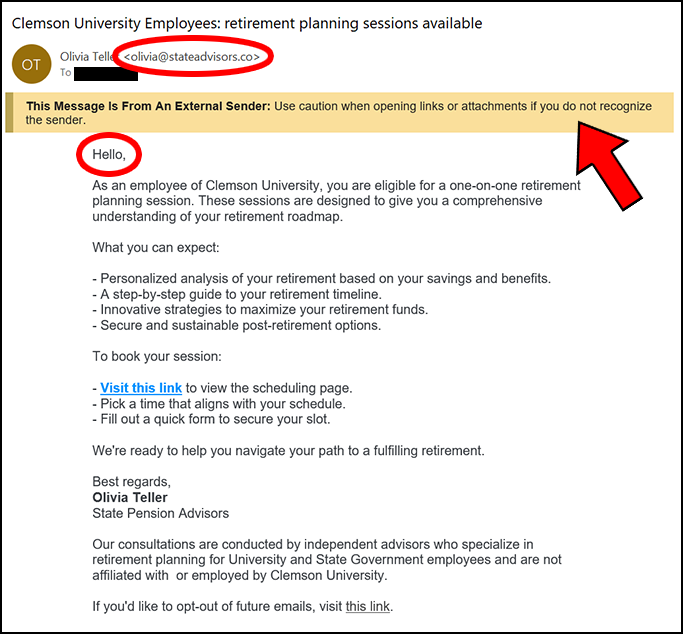
Retirement Planning Email
January 19, 2024
Many Clemson employees recently received an email like the one below. It encourages the recipient to follow a link and sign up for a session to help plan their retirement.
Clemson HR has verified that this is not a legitimate email from the SC Benefits program, which handles our state retirements. There is also a disclaimer in the email that says their representatives are independent and not state or university employees.
And there are several indicators in this email showing that it is not an official Clemson correspondence.
- The sender’s email address is not “clemson.edu” or “sc.gov”
- The greeting is generic and doesn’t use your name
- The External Sender banner is displayed, meaning that it is coming from an outside source.
Be aware that if you respond to this email, you will be dealing with a non-Clemson entity, and you should exercise extreme caution about sharing any personal or financial information.
Messaging App Scam
January 2, 2024
 Messaging apps, like WhatsApp, are being used by cybercriminals to target potential victims in cryptocurrency scams. Unlike other scams, this one begins as a friendly relationship, where the cybercriminal will attempt to develop a sort of friendship for a few weeks. It can even be posing as an accidental wrong number contacting you.
Messaging apps, like WhatsApp, are being used by cybercriminals to target potential victims in cryptocurrency scams. Unlike other scams, this one begins as a friendly relationship, where the cybercriminal will attempt to develop a sort of friendship for a few weeks. It can even be posing as an accidental wrong number contacting you.
According to a recent article on CNN, after weeks of back and forth friendly updates, the cybercriminals will send links to download an app that appears as legitimate cryptocurrency account software. Victims who have fallen for these scams have lost enormous amounts of money.
The Clemson University campus community is encouraged to practice due diligence and not engage with messages from unknown or unexpected contacts. Additionally, users should avoid clicking on links in messages from unknown sources.
Payroll Phishing
December 13, 2023
 Cybercriminals commonly use the topic of “payroll” as a scam. It is always important that you look carefully at the email sender’s address before responding to it or clicking on any link in an email.
Cybercriminals commonly use the topic of “payroll” as a scam. It is always important that you look carefully at the email sender’s address before responding to it or clicking on any link in an email.
All legitimate Clemson emails related to an employee’s payroll information will only come from either payroll@clemson.edu or CUBS2000@clemson.edu.
Clemson’s Human Resources department may send out emails for such things as:
- W2 and Year End reminders.
- Reminders to change your mailing address if you are moving.
- Weekly Payroll Reminders targeted to payroll end-users.
- To an employee, if their direct deposit is returned.
- To an employee, if they have a physical check that they need to pick up.
But do not trust any email that is not from either payroll@clemson.edu or CUBS2000@clemson.edu.
If you do receive a suspicious email, please report it to the Clemson Security Operations Center using the Report Phishing button in Outlook or by forwarding it to phishing@clemson.edu.
Fake MyBenefits Text Scam
November 10, 2023
The South Carolina Department of Employment and Workforce (SCDEW) is warning all users to be aware of a new scam done through phone text messages. These phishing text messages provide a website link to a phony webpage that was designed to look like the actual SC MyBenefits Portal website.
 If you receive one of these fake text messages on your phone, do not click on the link. Instead, you should delete the text message.
If you receive one of these fake text messages on your phone, do not click on the link. Instead, you should delete the text message.
Never click website links in text messages because they are not typically trustworthy. If you do need to visit a website for any reason, it is always better to open a browser yourself and type in the website address that you want, rather than trusting a link in a text message or email.
To interact with the actual SC MyBenefits Portal page, the official website address is https://dew.sc.gov/.
Pay Schedule – Phishing
November 9, 2023
Clemson’s Security Operations Center has detected a new phishing email that is targeting employees. In this campaign, the cybercriminals are trying to impersonate “Payroll Clemson” with an email similar to the one below. In this email, employees are asked to click on a button that takes them to a fake Clemson login page.
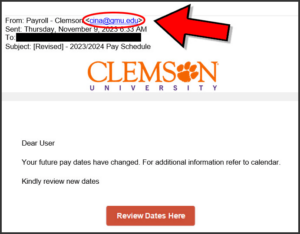 These cybercriminals are hoping that unsuspecting users will enter their Clemson login and password information. Then the bad actors could exploit the user’s account information by logging into any Clemson system and impersonating them for a variety of nefarious reasons.
These cybercriminals are hoping that unsuspecting users will enter their Clemson login and password information. Then the bad actors could exploit the user’s account information by logging into any Clemson system and impersonating them for a variety of nefarious reasons.
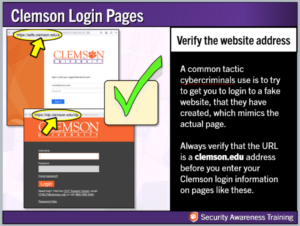
Users should be extra cautious when entering your Clemson login and password information. Always check the login page’s URL address to verify that it is a “clemson.edu” address before entering your account information.
And please report any suspicious email by using the Report Phishing button in Outlook or forwarding it to phishing@clemson.edu.
Holiday Scams
November 2, 2023
 During the holiday season, there is an increase in cybercriminal scams because there is also an increase in online shopping, donating to charities, using social media as well as more package deliveries. Let’s look at some common scams to be aware of this holiday season.
During the holiday season, there is an increase in cybercriminal scams because there is also an increase in online shopping, donating to charities, using social media as well as more package deliveries. Let’s look at some common scams to be aware of this holiday season.
Online Shopping Scams
Don’t be tempted by an email promising amazing prices or deals on popular holiday items. If a deal looks to good to be true, then it probably isn’t. These types of email scams will use a link to a fake website that may look real. But don’t click on website links within emails because they can be misleading. A better practice is to open a browser yourself and navigate to a specific website.
Another thing to look for when shopping online is that the URL of the website begins with HTTPS and not just HTTP. The HTTPS websites use encryption to help protect your confidential data such as your credit card information.
Also, carefully examine any website before you make a purchase. Verify that the design looks right, and the information seems legitimate. If anything is suspicious, you may be on a fake copy of the website.
Charity Scams
This scam is usually initiated through an unsolicited email. The cybercriminals are hoping that you will want to help with whatever the charitable event may be, and they will encourage you to send funds. But doing so, will only give your money to the cybercriminals. Although there are legitimate charities to support during the holidays, it is safer to browse to the official website of a charity yourself, rather than using a link within an email. So, always investigate before you donate.
Beware of people sharing content
The holiday season is also is a time when people want to share more articles, pictures, and videos with their friends and family. Cybercriminals know this and will try to infect shareable content with malware. It may be a file attached to an email message or it could be a link to a website that prompts you to update software to watch a video. Files shared by friends and family are believed to be safe, but they could have been infected with malware before it even reached someone you know as content is passed around. You should always be cautious when opening email attachments or clicking on links in emails. Because even though it may be a cute video of puppies doing something funny, you really don’t know where it’s been or if its infected.
Package Delivery Scams
This scam begins with an email or text message claiming that a company such as FedEx or Amazon was unable to deliver a package to your address. The message will typically provide a website link where you are asked for personal information such as your home delivery address. They may claim there is a “redelivery fee” and ask for your credit card information. But these can be scams that allow cybercriminals to steal your personal and financial information. Some of the fake websites even provide a means for the cybercriminals to install malware on your device. If you receive an email or text notification about a delivery issue, do not use the link in the message. Instead, directly contact the delivery company yourself to verify that there really is a delivery issue.
QR Code Scam
September 19, 2023
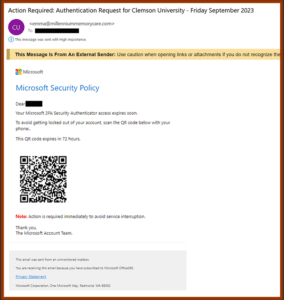
Clemson employees are now seeing a QR Code Scam email like the one below claiming to be from Microsoft. It tells the user that their Security Authenticator access is expiring soon. And to avoid being locked out of their account, they need to use their phone to connect to a QR code listed in the email. But this is a scam.
There are several indicators that this email is not legitimate. One is that the sender’s email is actually “emma@millenniummemorycare.com” which is not Microsoft. There is also a sense of urgency claiming that if you don’t act within 72 hours your account will be locked. They hope you won’t be thinking clearly if you are under pressure. Additionally, they want to move the scam from email to your phone, where you are less protected.
QR Codes were created as an easy and quick way to share a website URL. Rather than having to type in a website address, users could use the camera on their cell phone to scan the QR code and then seamlessly navigate to that web page.
But cybercriminals are abusing this convenience to get unsuspecting users to their malicious web pages. These phony websites could ask you to login to a service, exposing your account login and password information. Or you may be prompted to enter other sensitive information that they would steal and use in their attacks. These malicious web pages could also contain viruses and other malware which could infect your device, just by browsing to that web page. So be extra cautious with QR Codes.
Avoiding QR Code Scams:
- If you receive a suspicious email with a QR Code, use the Report Phishing button in Outlook to have the Clemson Security Operations Center review and investigate the email for you.
- Beware of QR Code stickers in public locations. Cybercriminals often will put their own malicious sticker on top of legitimate QR Codes in parking garages, on signs, ATMs, public posters, inside local businesses, and other locations.
- Always avoid using a QR code for doing any kind of fund or money transfer.
Research Job Scam
September 5, 2023
With the beginning of the Fall semester, Clemson students are being targeted again with a phishing email offering a fake job. The current scheme pretends to be from the Office of Sponsored Programs. And it offers a phony Research Position with a weekly pay of $350.
Here are the indicators that this is not a legitimate email:
-
- The sender’s email address is not a “Clemson.edu” address. And they even ask you to respond to a different external Gmail email address.
- Clemson Faculty will not typically reach out to our students with internship or job offers in this manner.
- The email has a sense of urgency stating that there are limited slots for this position. They are actually hoping that you won’t be thinking clearly, if you are in a rush.
- Plus they are prompting you to give them personal information, which they could use in a later attack. And they are wanting you to use an alternate personal email so that Clemson can’t block it.
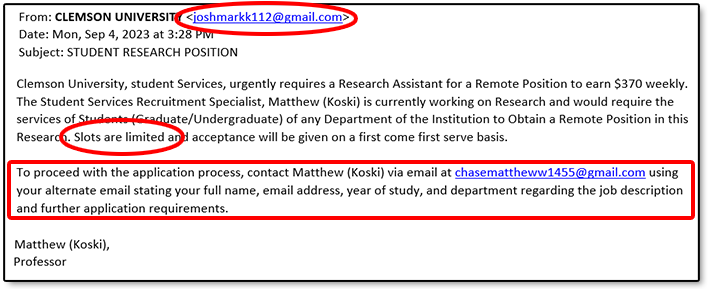
If you receive an email such as the one above, please report it to the Clemson Security Operations Center by forwarding the email to phishing@clemson.edu or by using the Report Phishing button in Outlook.
Smishing Top 5
July 14, 2023
 Smishing is using phone text messages to trick people into giving away personal information, account and password credentials, credit card or bank data, and other schemes. What these scams typically have in common is that they will imply a sense of urgency as well as impersonate someone you know or a business that you interact with, such as your bank or a service like Amazon. Cybercriminals like to target text messages because people typically respond more to text messages than any other form of communication.
Smishing is using phone text messages to trick people into giving away personal information, account and password credentials, credit card or bank data, and other schemes. What these scams typically have in common is that they will imply a sense of urgency as well as impersonate someone you know or a business that you interact with, such as your bank or a service like Amazon. Cybercriminals like to target text messages because people typically respond more to text messages than any other form of communication.
Here is a list of the most common smishing scams according to the Federal Trade Commission.
Fake Bank Fraud Alert
These text messages will typically ask you if you’ve made a specific high-dollar purchase or did a money transfer that you don’t recognize. And the text may simply ask you to confirm Yes or No about the transaction. Later, you will get follow-up texts and even phone calls claiming that they represent your bank or credit card. And that they want to help you with this fraud. But they may ask you to confirm account information or to reveal other sensitive data. They may even try to get you to transfer additional funds.
Amazon Security Alerts
Similar to the Band Fraud alerts, these text messages claim to be from Amazon and want to “alert” you about some suspicious activity on your account. Or ask you to confirm an expensive Amazon purchase that you won’t recognize. These messages may also include a URL link or phone number that they want you to use to respond to or communicate about this alert. But they will use that as a way to get personal and account information from you. For any service that you have like this, it is always better to open a browser yourself, login to your account and see if there really is an issue, rather than trust a link or phone number from a text.
Free Gift Reward
These “free gift” texts often pitch that you’ve won a free prize. Or that you are being rewarded for something like paying your bill on time, or some other scheme. They are hoping that victims will reveal personal information when they are asked to claim their prize, which will put you at risk for identity theft. Or they may say that there is a small payment to cover shipping costs and they will try to get you to expose your banking or credit card information.
Bogus Job Offer
Cybercriminals often scan employment websites looking for contact information and they will send a text message about a bogus job offer. You should always be suspicious of job offers from a text message. But one easy way to spot a scam is when they offer to send you a check for some amount with instructions for you to send part of those funds to a different address for training, materials, or some other items.
Fake Package Delivery Issues
With the large number of online orders that consumers now do, sending a text about a package delivery might seem very common and not out of the ordinary. Plus, consumers would be motivated to respond because they are usually anxious to get their packages. Cybercriminals often try to impersonate the U.S. Postal Service, FedEx, or UPS. The text will usually claim that there is a problem with making the delivery and will provide a link in the text message for you to resolve the issue. Some scams will simply ask you to pay an additional 30 cents to cover a postage error. But once you give your credit card information, they have all they need to make purchases with your card.
Key points to remember:
- Be suspicious of any text message that asks you to provide personal or account information.
- Do not click on any links or call the number shown in a text message. Instead, open a browser yourself and go to the service website yourself. Or contact the service provider via a known and verified phone number.
- And one of the best ways to avoid Smishing is by not responding to any text message unless it is from someone that is already in your phone’s Contact List.
Voice Stealing in 3 Seconds
April 26, 2023
 The Federal Trade Commission is warning people to be cautious about answering phone calls from unknown numbers. Threat actors are now recording your voice and then using Artificial Intelligence (AI) to convert those samples into realistic impersonations of you. They will use this impersonation to call one of your family members and sound like you. In their scam, they can claim to need help because they wrecked a car, are in the hospital, have been arrested, or any kind of circumstance. Then they typically will ask for money to help them with this make-believe situation. And the caller will sound just like you.
The Federal Trade Commission is warning people to be cautious about answering phone calls from unknown numbers. Threat actors are now recording your voice and then using Artificial Intelligence (AI) to convert those samples into realistic impersonations of you. They will use this impersonation to call one of your family members and sound like you. In their scam, they can claim to need help because they wrecked a car, are in the hospital, have been arrested, or any kind of circumstance. Then they typically will ask for money to help them with this make-believe situation. And the caller will sound just like you.
It only takes about three seconds for cybercriminals to sample enough of your voice to impersonate you. It could be as easy as you saying, “Hello? Who is this?” They can also pull samples of your voice from videos that you have posted on social media if your account is public.
So, if you decide to answer a call from an unknown number, always let the other person speak first. Or simply don’t answer a call from someone who is not on your phone’s contact list. And don’t trust a voice, just because it sounds like the person you know.
For more information, please see the Federal Trade Commission article.
Juice Jacking
April 18, 2023
The FBI is again warning people to avoid using public phone charging stations in airports, malls, hotels, or any public location, because of Juice Jacking.
 Juice Jacking is a way to compromise devices such as tablets or phones that use the same cable for charging as they do for data transfer. Hackers have figured out a way to put malware and monitoring software on your device as well as steal sensitive data when you use one of their modified charging stations. Even being connected for 60 seconds can be enough to compromise your device.
Juice Jacking is a way to compromise devices such as tablets or phones that use the same cable for charging as they do for data transfer. Hackers have figured out a way to put malware and monitoring software on your device as well as steal sensitive data when you use one of their modified charging stations. Even being connected for 60 seconds can be enough to compromise your device.
Here are a few indicators that your device may have been hacked, although it is usually difficult to tell.
- Apps take a long time to load.
- Your device frequently crashes.
- The device has excessive overheating.
- There is increased or unusual data usage.
The best way to avoid Juice Jacking is to always use your own charger and cable connected to a standard outlet. You can also purchase a Data Blocker adaptor that clips onto the end of your standard cable or even purchase a special cable that only allows for power and no data transfer.
Retirement Meeting Scam
April 14, 2023
Recently, some Clemson employees received an email like the one below prompting users about their retirement options. The email offered a free one-on-one consultation and provided a link to schedule a meeting.
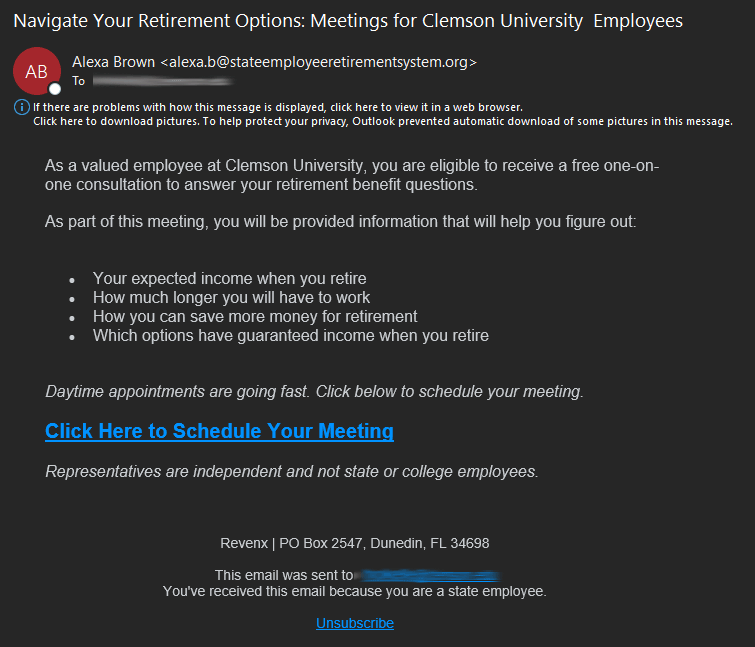 This email was actually a phishing scam designed to gather and steal personal information. Clemson’s Office of Information Security has already taken steps to remove and block this specific email.
This email was actually a phishing scam designed to gather and steal personal information. Clemson’s Office of Information Security has already taken steps to remove and block this specific email.
But you should always be cautious about emails asking you for information, especially ones that may ask you to login to a page. One of the clues that this email was fraudulent is that it came from a non-Clemson email address.
If you receive a suspicious email, always report it by using the Report Phishing button in Outlook or forward it to phishing@clemson.edu.
Password Strength
April 11, 2023
 As computing power continues to increase along with the growth of Artificial Intelligence, it is becoming easier to crack user’s passwords. Having a longer, more complex, and unique password for your account is vital.
As computing power continues to increase along with the growth of Artificial Intelligence, it is becoming easier to crack user’s passwords. Having a longer, more complex, and unique password for your account is vital.
A recent study by Home Security Heroes has shown how quickly passwords can be broken.
| # of Characters | Numbers Only | Lowercase Letters | Lowercase Upper & Letters | Numbers, Upper & Lowercase Letters | Numbers, Upper & Lowercase Letters, Symbols |
|---|---|---|---|---|---|
| 4 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 5 | Instantly | Instantly | Instantly | Instantly | Instantly |
| 6 | Instantly | Instantly | Instantly | Instantly | 4 Seconds |
| 7 | Instantly | Instantly | 22 Seconds | 42 Seconds | 6 Minutes |
| 8 | Instantly | 3 Seconds | 19 Minutes | 48 Minutes | 7 Hours |
| 9 | Instantly | 1 Minute | 11 Hours | 2 Days | 2 Weeks |
| 10 | Instantly | 1 Hour | 4 Weeks | 6 Months | 5 Years |
| 11 | Instantly | 23 Hours | 4 Years | 38 Years | 356 Years |
| 12 | 25 Seconds | 3 Weeks | 289 Years | 2 K Years | 30 K Years |
| 13 | 3 Minutes | 11 Months | 16 K Years | 91 K Years | 2 M Years |
| 14 | 36 Minutes | 49 Years | 827 K Years | 9 M Years | 187 M Years |
| 15 | 5 Hours | 890 Years | 47 M Years | 613 M Years | 14 Bn Years |
| 16 | 2 Days | 23 K Years | 540 M Years | 26 Bn Years | 1 Tn Years |
| 17 | 2 Weeks | 812 K Years | 2 Bn Years | 2 Tn Years | 95 Tn Tears |
| 18 | 10 Months | 22 M Years | 7.23 Bn Years | 96 Tn Years | 6 Qn Years |
Things to Remember:
- The Clemson Account and Password Management Policy states that
“Each user is responsible for creating strong passwords and safeguarding the IT Credentials of the User.” - Password length and complexity are key to its strength.
- Do not re-use the same password on different accounts.
- Avoid using Public Wi-Fi, especially when you need to login to accounts.
To update your Clemson password, use the Password Change Utility.
Smishing Texts
February 9, 2023
Clemson and several other Universities are seeing an increase in phone texting scams which is called Smishing. These phone text messages impersonate someone you know, like President Clements or a Department head, but are typically from an unknown number.
 These text messages usually begin by asking for a favor, with an excuse that they are too busy to do the task themselves. It can be a request for information or something like the purchase of a gift card.
These text messages usually begin by asking for a favor, with an excuse that they are too busy to do the task themselves. It can be a request for information or something like the purchase of a gift card.
Cybercriminals will often target specific groups of users and will try to impersonate someone who is known to that group.
Phone Texting has become a new focus for cybercriminals because people typically read 98% of texts and also respond to 45% of those messages. In comparison, email messages are read only 20% of the time and responded to about 6%. Plus, when people are on their phones, they are usually more distracted, which makes them more likely to fall for one of these scams.
Key points to remember:
- Be suspicious of any text message that asks you to provide personal or account information.
- Never provide your password in response to a text.
- Do not click on any links or call the number shown in a text message.
- When in doubt about a text, contact the actual person yourself through a reliable source, such as the Clemson online phonebook, before taking any action.
- And one of the best ways to avoid Smishing is by not responding to any text message unless it is from someone that is already in your phone’s Contact List.
If you do receive one of these suspicious text messages, please report it to the Clemson Office of Information Security at phishing@clemson.edu.
Office Supply Scam
January 24, 2023
 Clemson students are being targeted with an email scam that promises a paycheck for office supplies.
Clemson students are being targeted with an email scam that promises a paycheck for office supplies.
In this email phishing campaign, the cybercriminals are impersonating a Clemson professor. One of the indicators that this is not a legitimate email is that it is from a Gmail address instead of a clemson.edu account. If you receive a suspicious email, it is a recommended that you contact the sender through a reliable source such as the Clemson Online Phonebook, rather than respond directly to the email.
Below is an example of one of the scammer’s emails.
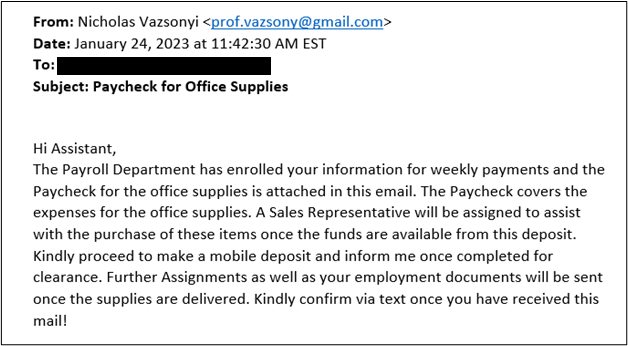
If you receive an email like this, please report it to the Clemson Security Operations Center by forwarding the email to phishing@clemson.edu. Then delete it.
Document Shred Event
November 14, 2022
 On Monday November 14th you can bring your work or personal documents to be shredded from 10am – 2pm at LittleJohn Coliseum. Secure shredding services will be provided by the Shred360 company.
On Monday November 14th you can bring your work or personal documents to be shredded from 10am – 2pm at LittleJohn Coliseum. Secure shredding services will be provided by the Shred360 company.
They are only accepting paper documents for shredding for this event. But staples, paper clips, binders, and notebooks can be shredded with the paper material. Hazardous waste and electronics will not be accepted. Attendees can bring up to 3 file boxes or 3 kitchen trash bags of material.
This is a one-day free event, and open to the public. Our goal is to bring awareness toward information protection, and the responsible destruction of sensitive files and records.
Apple Updates Needed
August 19, 2022
 Apple has released critical updates for MacOS, iOS, iPadOS and their Safari browser. These updates address actively exploited vulnerabilities. And users are encouraged to download and install these updates as soon as possible.
Apple has released critical updates for MacOS, iOS, iPadOS and their Safari browser. These updates address actively exploited vulnerabilities. And users are encouraged to download and install these updates as soon as possible.
Here are the latest versions that they recommend you should be using:
- macOS 12.5.1
- iOS 15.6.1
- iPadOS 15.6.1
- Safari 15.6.1
Additional information can be found on the Apple website.
Text Scam
July 5, 2022
Clemson is seeing an increase in phone text scams targeting specific groups. These phone text messages impersonate someone you know, like President Clements or a Department head, but are typically from an unknown number.
 The text messages usually begin by asking for a favor, with an excuse that they are too busy to do the task themselves. It can be a request for information or something like the purchase of gift cards.
The text messages usually begin by asking for a favor, with an excuse that they are too busy to do the task themselves. It can be a request for information or something like the purchase of gift cards.
Cybercriminals often target specific groups of users and will try to impersonate someone who is known to that group.
Any time you receive a suspicious request, whether it is from a text message, an email or a phone call, it is always a good practice to verify the request. Contact the actual person through a reliable source, such as the Clemson online phonebook, before taking any action.
If you do receive one of these suspicious requests, please report it to the Clemson Office of Information Security at phishing@clemson.edu.
Job Offer Scam
June 20, 2022
 Please be aware that there has been an increasing number of email scams targeting our Clemson students. These emails are typically for job offers or internships that promise a weekly paycheck of $300-$400. And it is often signed by someone impersonating a university professor.
Please be aware that there has been an increasing number of email scams targeting our Clemson students. These emails are typically for job offers or internships that promise a weekly paycheck of $300-$400. And it is often signed by someone impersonating a university professor.
Below is an example of one of the scammer’s emails. Please note that the sender’s email address is not a Clemson account. Also, keep in mind that Clemson Faculty will not typically reach out to our students with internship or job offers in this manner.
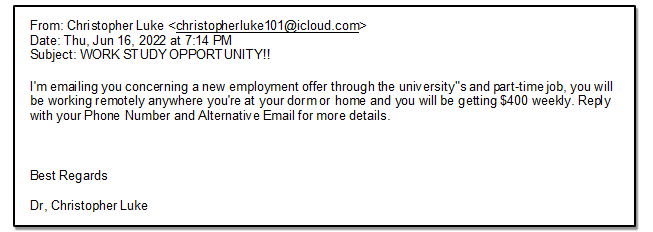
If you receive an email such as the one above, please report it to the Clemson Security Operations Center by forwarding the email to phishing@clemson.edu.
Gift Card Scam
May 19, 2022
 Students are being targeted by a new email phishing campaign. In this scheme, the cybercriminals are impersonating Clemson faculty and asking students for information. The typical pattern would be that if you respond to the email, they will attempt to trick you into buying gift cards for them or disclosing your bank account information.
Students are being targeted by a new email phishing campaign. In this scheme, the cybercriminals are impersonating Clemson faculty and asking students for information. The typical pattern would be that if you respond to the email, they will attempt to trick you into buying gift cards for them or disclosing your bank account information.
To help avoid this scam:
- When in doubt, contact the sender yourself by looking up their contact information from a reliable source such as the Clemson Online Phonebook.
- Always look carefully at the sender’s email address. Most email scams don’t come from a “@clemson.edu” address.
- And never click links in an email that direct you to a website where you’d have to login and authenticate.
If you receive a phishing email like this, do not respond or give any information. Instead, report it by forwarding it to ithelp@clemson.edu. And then, simply delete the email.
Please exercise heightened awareness.
Phone Spoofing
May 19, 2022
 University phone numbers are being used in a new Phone Spoofing campaign where cybercriminals are trying to trick our users into revealing information.
University phone numbers are being used in a new Phone Spoofing campaign where cybercriminals are trying to trick our users into revealing information.
Phone Spoofing is when a caller deliberately falsifies their caller information so that their call appears to be from someone else. Scammers use this method to try and impersonate a phone number that you might recognize in order to convince you to give them valuable information.
In this latest campaign, the scammers were impersonating Clemson 656-xxxx numbers and targeting Clemson employees.
Since the Clemson Phone Systems are not being utilized as part of this scam, we have no way of blocking these fraudulent calls. If you receive one of these Phone Spoofing calls, please collect as many details regarding the incident as you can and send that information to ithelp.clemson.edu.
Critical Apple Updates
April 4, 2022
 Apple has just released new security updates to address two zero-day vulnerabilities that can be exploited by attackers targeting iPhones, iPads, and Macs.
Apple has just released new security updates to address two zero-day vulnerabilities that can be exploited by attackers targeting iPhones, iPads, and Macs.
iPhones and iPads devices should be upgraded to version 15.4.1 or higher. For non-mobile devices, MacOS Monterey 12.3.1 or higher is required to be safe. In addition, tvOS and watchOS also have updates available.
Users are advised to update their Apple devices as soon as possible.
For additional information you can visit: https://support.apple.com/en-us/HT213219
Chrome & Edge Updates
March 29, 2022
 Google released another critical update to address a zero day security issue. This vulnerability would potentially allow attackers to access unauthorized data and execute malicious code.
Google released another critical update to address a zero day security issue. This vulnerability would potentially allow attackers to access unauthorized data and execute malicious code.
If you are running Chrome version 99.0.4844.84 or higher, then your version is up to date. If not, then follow the steps below to update your Chrome browser.
Microsoft has also confirmed that Edge, a Chromium-based browser, is also affected by this vulnerability. Edge users should update their browsers to version 99.0.1150.55, to protect themselves from this vulnerability.
How to Update Chrome:
- On your computer, open Chrome.
- In the upper right corner of the browser, click on the 3 vertical dots for the Menu.
- Select Help. And click About Google Chrome.
- Then click the Update Google Chrome
Note: If you can’t find this button, you’re on the latest version. - Click Relaunch.
How to Update MS Edge:
- Click the Menu button in the top-right corner of the screen.
- Hover over the “Help and Feedback” menu item.
- Click “About Microsoft Edge”.
- Edge will automatically check for updates.
Additional information can be found here:
https://blog.malwarebytes.com/exploits-and-vulnerabilities/2022/03/update-now-google-releases-emergency-patch-for-chrome-zero-day-used-in-the-wild/
Critical Chrome Update
February 15, 2022
 Google has just released an urgent patch for the Chrome web browser. This new Chrome version fixes several security issues, one of which is being exploited actively according to Google. Google does not mention how widespread the attacks are, but Chrome users are highly encouraged to update to the latest version as soon as possible.
Google has just released an urgent patch for the Chrome web browser. This new Chrome version fixes several security issues, one of which is being exploited actively according to Google. Google does not mention how widespread the attacks are, but Chrome users are highly encouraged to update to the latest version as soon as possible.
If you are running Chrome version 98.0.4758.102 or higher, then your version is updated. If not, then follow the steps below to update your Chrome browser.
How to Update Chrome:
- On your computer, open Chrome.
- In the upper right corner of the browser, click on the 3 vertical dots for the Menu.
- Select Help. And click About Google Chrome.
- Then click the Update Google Chrome
Note: If you can’t find this button, you’re on the latest version. - Click Relaunch.
Additional information can be found here:
https://blog.malwarebytes.com/exploits-and-vulnerabilities/2022/02/update-now-chrome-patches-actively-exploited-zero-day-vulnerability/
Email Spoofing Attacks
January 19, 2022
Recently, Clemson users have been the target of Email Spoofing. Email Spoofing is when you receive an email that is made to look like it is from someone you may know or trust. The cybercriminal using this technique want you to divulge personal information or have you to take some action.
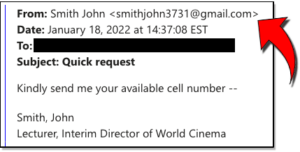 In this latest campaign, Clemson users were prompted to reply to the fake email with their cell phone number. Although at first glance the email may appear to be a simple request, it is really a trick to get your cell phone number. The cybercriminal can then either sell your phone number to another cybercriminal or use it themselves for their next targeted attack. Essentially, what they are doing is seeing who might fall for the fake email and then consider them an easier target for a follow up phone call.
In this latest campaign, Clemson users were prompted to reply to the fake email with their cell phone number. Although at first glance the email may appear to be a simple request, it is really a trick to get your cell phone number. The cybercriminal can then either sell your phone number to another cybercriminal or use it themselves for their next targeted attack. Essentially, what they are doing is seeing who might fall for the fake email and then consider them an easier target for a follow up phone call.
According to ProofPoint, an American enterprise security company, there are 3.1 billion spoofing emails sent each day and more than 90% of cyber-attacks start with an email message.
How to protect yourself from Email Spoofing:
- Always look carefully at the sender’s email address. Most email scams don’t come from a “@clemson.edu” address.
- When in doubt, contact the sender yourself by looking up their contact information from a reliable source such as the Clemson Online Phonebook.
- Never click links in an email that direct you to a website where you’d have to login and authenticate.
- Don’t open any attachments that you didn’t expect or are from unknown sources.
And always report any suspicious email to the Office of Information Security, by clicking on the Report Phishing button in Outlook or forwarding it to phishing@clemson.edu
Log4j Exploit
December 15, 2021
 What is Log4j ?
What is Log4j ?
Log4j is an open source Java logging library that was developed by the Apache Foundation. It is used in a large number of commercial software applications and services.
Problem
A vulnerability has been discovered in the Apache Log4j utility that could give cybercriminals the ability to perform remote code execution on vulnerable systems. This vulnerability is impacting organizations all over the world.
Solution
Clemson’s Office of Information Security is investigating and addressing this issue. CCIT System Administrators are actively working to resolve any vulnerabilities. And vendors are working to provide updates for this vulnerability as quickly as possible.
Additional Technical Information
For details, see Apache Log4j Security Vulnerabilities.
If you have any additional questions, please contact the CCIT Support Desk at ITHelp@clemson.edu or 864-656-3494.
Beware of Holiday Scams
November 29, 2021
 During the holiday season, there is an increase in cybercriminal scams because there is also an increase in online shopping, donating to charities, using social media as well as more package deliveries. Let’s look at some common scams to be aware of this holiday season.
During the holiday season, there is an increase in cybercriminal scams because there is also an increase in online shopping, donating to charities, using social media as well as more package deliveries. Let’s look at some common scams to be aware of this holiday season.
Online Shopping Scams
Don’t be tempted by an email promising amazing prices or deals on popular holiday items. If a deal looks to good to be true, then it probably isn’t. These types of email scams will use a link to a fake website that may look real. But don’t click on website links within emails because they can be misleading. A better practice is to open a browser yourself and navigate to a specific website.
Another thing to look for when shopping online is that the URL of the website begins with HTTPS and not just HTTP. The HTTPS websites use encryption to help protect your confidential data such as your credit card information.
Also, carefully examine any website before you make a purchase. Verify that the design looks right, and the information seems legitimate. If anything is suspicious, you may be on a fake copy of the website.
Charity Scams
This scam is usually initiated through an unsolicited email. The cybercriminals are hoping that you will want to help with whatever the charitable event may be, and they will encourage you to send funds. But doing so, will only give your money to the cybercriminals. Although there are legitimate charities to support during the holidays, it is safer to browse to the official website of a charity yourself, rather than using a link within an email. So, always investigate before you donate.
Beware of people sharing content
The holiday season is also is a time when people want to share more articles, pictures, and videos with their friends and family. Cybercriminals know this and will try to infect shareable content with malware. It may be a file attached to an email message or it could be a link to a website that prompts you to update software to watch a video. Files shared by friends and family are believed to be safe, but they could have been infected with malware before it even reached someone you know as content is passed around. You should always be cautious when opening email attachments or clicking on links in emails. Because even though it may be a cute video of puppies doing something funny, you really don’t know where it’s been or if its infected.
Package Delivery Scams
This scam begins with an email or text message claiming that a company such as FedEx or Amazon was unable to deliver a package to your address. The message will typically provide a website link where you are asked for personal information such as your home delivery address. They may claim there is a “redelivery fee” and ask for your credit card information. But these can be scams that allow cybercriminals to steal your personal and financial information. Some of the fake websites even provide a means for the cybercriminals to install malware on your device. If you receive an email or text notification about a delivery issue, do not use the link in the message. Instead, directly contact the delivery company yourself to verify that there really is a delivery issue.
Caution with DUO
November 15, 2021
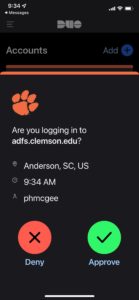 If you receive a DUO authentication request on your mobile device for system access that you did not just initiate yourself, do not approve it.
If you receive a DUO authentication request on your mobile device for system access that you did not just initiate yourself, do not approve it.
It may be someone else trying to login to your account who has stolen your login and password.
Clemson uses DUO for two-factor authentication, to protect against unauthorized access to University systems and services. DUO provides a second layer of security.
Here’s a typical cybercriminal process:
- Obtain a Clemson user’s login and password through a phishing email or other social engineering scam
- Login to the University Email System using the stolen account information
- The University Email System requires secondary authentication via DUO, which sends a push notification to the Clemson user
- Clemson user receives notification on their mobile device asking for access to their account
If the Clemson user approves this DUO request, then the cybercriminal will be logged in and can assume the identity of the Clemson user.
In summary, never approve a DUO authentication request, that you did not just initiate yourself.
Phone Scam
November 10, 2021
 There is a new Phone Spoofing campaign targeting Clemson users where scammers are trying to trick people into revealing information related to a person’s position and their University financial responsibilities.
There is a new Phone Spoofing campaign targeting Clemson users where scammers are trying to trick people into revealing information related to a person’s position and their University financial responsibilities.
Phone Spoofing is when a caller deliberately falsifies their caller information so that their call appears to be from someone else. Scammers use this method to try and impersonate a phone number that you might recognize in order to convince you to give them valuable information.
In this campaign, the scammers were impersonating high level Clemson employee’s work phone numbers and targeting Clemson employees.
Since these calls are originating from outside 3rd party sources, we have no way of knowing the extent of this campaign. If you receive a call that you suspect could be a scam, end the call and call the listed phone number for that individual to verify. Please collect as many details regarding an incident as you can and send that information to security@clemson.edu.
New DUO Screen
October 18, 2021
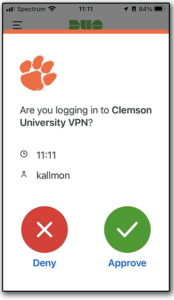 DUO has updated and redesigned the user interface on their DUO Mobile Application for both iOS and Android. After updating to version 4, users will see the new look. The functionality is basically the same, but the Push Approval prompt has been redesigned, as shown here.
DUO has updated and redesigned the user interface on their DUO Mobile Application for both iOS and Android. After updating to version 4, users will see the new look. The functionality is basically the same, but the Push Approval prompt has been redesigned, as shown here.
Another change is that users will now be asked if they are logging into the application that initiated the login prompt. And it will list some of the details associated with that request.
The placement of the buttons has also changed. The Deny button is now on the left, while the Approve button is on the right.
DUO has also provided a video highlighting all of these new changes, which can be found at: https://www.youtube.com/watch?v=vZY62LJRfdU
Critical Chrome Update
October 11, 2021
 Google has confirmed that there is another zero-day vulnerability that was discovered in their Chrome browser which currently has around 2.6 billion users. A zero-day exploit is a computer or software vulnerability that has been discovered before a patch or fix for that problem has been created. So, these types of threats can be more dangerous if users don’t do updates in a timely manner.
Google has confirmed that there is another zero-day vulnerability that was discovered in their Chrome browser which currently has around 2.6 billion users. A zero-day exploit is a computer or software vulnerability that has been discovered before a patch or fix for that problem has been created. So, these types of threats can be more dangerous if users don’t do updates in a timely manner.
In response to this latest threat, Google has released a critical update patch for Chrome. But Google does warn that the rollout of this update will be staggered, which means that not everyone will be able to protect themselves immediately.
Anyone who does have Chrome installed, should open that program and go to the menu which can be accessed by clicking on the three vertical dots in the upper right corner of the browser. Select Settings from the list, then click on About Chrome from the left menu. If you are running Chrome version 95.0.4638.54 or higher, then your version is updated. If not, then follow the prompts for updating which will require restarting the browser after the update.
Urgent Apple Update
September 14, 2021
 This week, the Apple vendor distributed an urgent update patch for iOS and macOS to address a zero-day malware attack involving the FORCEDENTRY exploit.
This week, the Apple vendor distributed an urgent update patch for iOS and macOS to address a zero-day malware attack involving the FORCEDENTRY exploit.
This malware can impact iPhones, iPads, Apple Watch, iPod Touch and Mac computer devices. And it can infect your Apple device without you ever knowing it. Although it was just recently discovered, the more than 1.65 billion Apple products in use worldwide have been vulnerable to this spyware since at least March of this year.
This exploit installs spyware, called Pegasus, which can turn on the camera and microphone on your device, as well as record messages, texts, emails, and phone calls.
Be sure to check for OS updates and install them on all of your Apple devices to help prevent this potential cyber-attack.
Clemson Phone Spoofing
August 20, 2021
 Clemson phone numbers are being used in a new Phone Spoofing campaign where cybercriminals are trying to trick people into revealing Medicaid information.
Clemson phone numbers are being used in a new Phone Spoofing campaign where cybercriminals are trying to trick people into revealing Medicaid information.
Phone Spoofing is when a caller deliberately falsifies their caller information so that their call appears to be from someone else. Scammers use this method to try and impersonate a phone number that you might recognize in order to convince you to give them valuable information.
In this latest campaign, the scammers were impersonating a Clemson 656-xxxx number and targeting local senior citizens.
Since the Clemson Phone Systems are not being utilized as part of this scam, we have no way of knowing how widespread this campaign is. If you are contacted about one of these Clemson Phone Spoofing calls, please collect as many details regarding the incident as you can and send that information to security@clemson.edu.
Amazon Sidewalk Auto-Enrollment
June 3, 2021
 Beginning June 8, 2021, Amazon devices such as Alexa, Echo and others will by default enroll you in the Amazon Sidewalk service.
Beginning June 8, 2021, Amazon devices such as Alexa, Echo and others will by default enroll you in the Amazon Sidewalk service.
Amazon Sidewalk is a new wireless mesh service which will share some of your Internet service bandwidth with other nearby capable devices that don’t have connectivity. Essentially, you will be sharing your Internet network with them to help improve coverage.
This new Amazon Sidewalk service will include an encryption feature and the Sidewalk Network Server (SNS) does not know the contents of the packets or commands being sent over Sidewalk. And unique identifying credentials make sure trusted devices can enter the Sidewalk network while preventing unauthorized devices from joining.
But any wireless technology has increased security risks. Another consideration is that your Amazon devices also contain a large amount of personal information since they are tied to your home with things like your front door lock, cameras, home security systems and other sensitive information such as your Amazon shopping patterns.
If you’d rather not have your devices use this new service, you can opt-out of the Amazon Sidewalk service by doing the following:
- Opening the Alexa app
- Opening More and selecting Settings
- Selecting Account Settings
- Selecting Amazon Sidewalk
- Turning Amazon Sidewalk Off
Math Tutoring Scam
April 19, 2021
 Recently, some Clemson users were targeted with a Phishing Campaign. The email, which was sent from a Yahoo email account, claimed to be looking for an online math tutor for their son.
Recently, some Clemson users were targeted with a Phishing Campaign. The email, which was sent from a Yahoo email account, claimed to be looking for an online math tutor for their son.
The cybercriminals had done some research to try to make this phishing email seem more believable. The emails were specifically sent to some Clemson math majors and even referenced our Director from the School of Mathematical and Statistical Sciences by name.
This was not a legitimate email. Both the director, as well as students, have reported it. Typically, the cybercriminals will start with this type of introductory email to see if they can get anyone to respond. And if someone responds, then there is a variety of schemes they will use to either steal your information or funds.
When you suspect that an email may be Phishing, simply report it by using the Report Phishing button in Outlook, or forward it to phishing@clemson.edu.
To avoid becoming a victim of Phishing Emails, you should always do the following:
- Check the sender’s name and email address carefully
- Beware of email subjects asking for immediate action
- Be cautious of generic greetings
- Look for grammatical and spelling errors
- Be careful with website links or attachments
- When unsure about a Clemson email request, contact the user by phone to verify.
Fake IRS Scam is Targeting University Emails
April 1, 2021
 The IRS published a warning this week about an on-going Phishing Campaign that is specifically targeting anyone with a University or College email address which ends in “.edu.” This would include all Clemson Staff and Students.
The IRS published a warning this week about an on-going Phishing Campaign that is specifically targeting anyone with a University or College email address which ends in “.edu.” This would include all Clemson Staff and Students.
The cybercriminals are trying to impersonate the IRS and will use subject lines such as “Tax Refund Payment” or “Recalculation of your tax payment” in the phishing emails.
The email will state that in order to process your refund, you will need to click on a link in the email, which will take you to a form. The cybercriminals use this form to collect personal information such as your social security number, date of birth, driver’s license number, gross annual income, mailing address, or electronic filing PIN. If you submit any information, the cybercriminals could use it to steal your identity and even reroute your refund check to their account instead of yours.
You should always be extremely cautious about clicking links within an email because links in emails can be misleading. To check the validity of an email link, it is always safer to open your own browser and manually navigate to a website. For example, taxpayers who want to check on their refund status, should manually go to the official IRS website, IRS.gov, and click on the link for “Where’s My Refund” to ensure that they are on the correct website. Otherwise, you may end up on a cleverly engineered fake website, that was designed to steal your information.
If you receive a phishing email, do not click on any links within the email. Simply report it using the Report Phishing button in Outlook. Or forward it to phishing@clemson.edu. And then delete it.
For additional information, visit the IRS website at: https://www.irs.gov/newsroom/irs-warns-university-students-and-staff-of-impersonation-email-scam
Stealing Your Phone Texts
March 25, 2021
 There are legitimate services that were originally created to help businesses with marketing and sending mass communications through cell phone texts. But cybercriminals are now misusing this service to steal information by rerouting your text messages. With most of these rerouting services, there is an initial message sent to let the phone owner know that the text messages will be rerouted, but some companies do not send a notification. All mobile carriers and phone types are susceptible to this type of attack because the messages are intercepted before they are delivered to the phone. You may not even realize that there is a problem unless you notice that you are no longer receiving text messages.
There are legitimate services that were originally created to help businesses with marketing and sending mass communications through cell phone texts. But cybercriminals are now misusing this service to steal information by rerouting your text messages. With most of these rerouting services, there is an initial message sent to let the phone owner know that the text messages will be rerouted, but some companies do not send a notification. All mobile carriers and phone types are susceptible to this type of attack because the messages are intercepted before they are delivered to the phone. You may not even realize that there is a problem unless you notice that you are no longer receiving text messages.
Since many online services use phone texts to verify your identity, such as your banking accounts, a cybercriminal can easily request a password reset and then use the rerouted text message to authorize the password change and lock you out of your own account. This could also affect Clemson University’s DUO authentication if you choose the texting option for verification.
Whenever possible, avoid using text messages for authentication. As an alternative, use mobile apps for authentication that offer non-text confirmation msuch as Microsoft Authenticator, Google Authenticator, Duo Mobile, or other apps recommended by your account provider.
Job Offer Email Scam
February 24, 2021
 Some Clemson user are seeing an email offering the recipient a job position based on a claim that they reviewed the user’s resume from a Clemson Career Center upload. The Clemson user is instructed to setup a Telegram account and send information to their Hiring Manager at Cottage Health System.
Some Clemson user are seeing an email offering the recipient a job position based on a claim that they reviewed the user’s resume from a Clemson Career Center upload. The Clemson user is instructed to setup a Telegram account and send information to their Hiring Manager at Cottage Health System.
This is not a valid email and is part of a cybercriminal scam. Users should not reply to this email or click on any links within the email.
Employees who receive this email can report it using the Report Phishing button in Outlook. Students can forward it to phishing@clemson.edu. Once reported, users should delete the email.
 Cybersecurity
Cybersecurity